Preparation Manual
Section 4: Sample Selected-Response Questions
TX PACT: Technology Applications: Early Childhood–Grade 12 (742)
Expand All Answers | Collapse All Answers
This section presents some sample exam questions for you to review as part of your preparation for the exam. To demonstrate how each competency may be assessed, sample questions are accompanied by the competency that they measure. While studying, you may wish to read the competency before and after you consider each sample question. Please note that the competency statements do not appear on the actual exam.
The correct answer is provided for each sample exam question. The sample questions are included to illustrate the formats and types of questions you will see on the exam; however, your performance on the sample questions should not be viewed as a predictor of your performance on the actual exam.
Domain I—Foundations of Computers-Based Technology
Competency 001—Demonstrate a broad and comprehensive understanding of operations and concepts related to computers and technology.
1. On a local area network (LAN), a switch provides a significant advantage over a hub because a switch:
- amplifies the strength of a wireless signal so it can be carried through the network.
- decreases the number of errors that can occur during data transmission.
- transmits data only to the destination node rather than to all the nodes on the LAN.
- increases the number and variety of devices that can be connected to the LAN.
- Enter to expand or collapse answer 1.Answer expanded
- Option C is correct. This question requires the examinee to demonstrate knowledge of terminology and concepts related to computer networks. A local area network is a set of networked computers in a small area such as a school or business. A hub is a network component that receives a message and then repeats the message by sending it to every port on the network. This is inefficient and increases the probability of packet collisions. A switch, on the other hand, knows the location of each computer or device on the network. The switch analyzes each message and sends it directly to the intended network port or node. Switches are generally more efficient and help increase the speed of the network.
2. Which of the following actions best illustrates the concept of redundancy?
- Creating backup copies of software applications and storing them at an off-site location.
- Installing an array of mirrored hard drives in a network server.
- Creating a wireless network so users can use network peripherals from any location.
- Copying an identical image to the hard drive of every new computer purchased.
- Enter to expand or collapse answer.Answer expanded
- Option B is correct. This question requires the examinee to demonstrate knowledge of technology and concepts related to computers and technology. In technology and engineering, redundancy is the process of having multiple components or systems to perform the same task in case of a failure. The purpose of redundancy is to increase the reliability of a system by having a back-up process in place. Disk mirroring is the process of storing the same data on two or more hard drives. Having an array of mirrored disks is an example of a redundant system, since if one disk fails, then the data can always be retrieved from one of the other identical disks.
Competency 002—Demonstrate a broad and comprehensive understanding of the management of hardware and software resources.
3. The use of videoconferencing technology in a fourth-grade class would be most appropriate for which of the following purposes?
- Viewing virtual field trips to museums, cultural centers, or national monuments.
- Watching a prerecorded digital presentation that enhances an instructional unit.
- Communicating with students in another country so students can learn about each other's cultures.
- Recording and editing a digital movie of a class play that will be posted on the school's Web page.
- Enter to expand or collapse answer.Answer expanded
- Option C is correct. This question requires the examinee to demonstrate knowledge of the types of software used in educational settings. Videoconferencing software is used to facilitate communication by transmitting a variety of media between two or more remote sites. Of the responses given, the most appropriate use of videoconferencing software would be to connect with students in another country so they could maximize their interactions by sharing video, audio, and text information about their cultures in real-time.
4. A student has good composition skills but poor fine-motor skills. Which of the following types of assistive technology would best help this student create a written report?
- Communication board.
- Graphic organizer.
- Programmable keyboard.
- Joystick and light pen.
- Enter to expand or collapse answer.Answer expanded
- Option C is correct. This question requires the examinee to demonstrate knowledge of types and uses of adaptive assistive technology resources used in classroom settings. A programmable keyboard allows the user to change the keyboard layout to facilitate a child who has poor fine-motor skills. The ways that certain keys function can also be changed. For example, if a student tends to hold a key down too long on a regular keyboard, the letter will be repeated. The programmable keyboard can be adapted so that the letter will appear only once. Other features such as the response rate can be adjusted to help students who tend to strike multiple keys at the same time. These features can greatly facilitate the creation of a written report by allowing the student to focus on the composition rather than the typing of the text.
Domain II—Use of Computer-Based Technology
Competency 003—Demonstrate a broad and comprehensive understanding of concepts and skills related to the use of technology resources.
Use the diagram below to answer the question that follows. 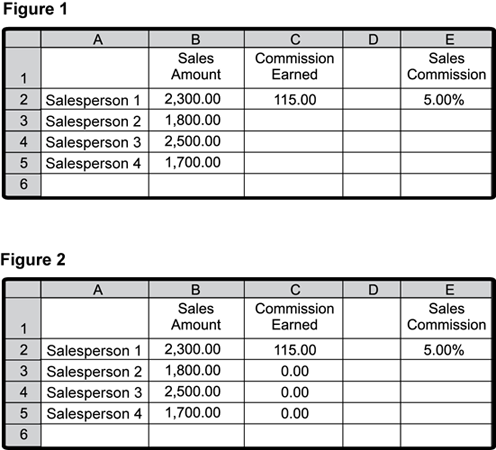
Figure 1 represents row 1 columns B, C, and E contain headers that say, in order from B, C, E: "Sales Amount," "Commissions Earned," and "Sales Commission." In subsequent rows, some cells contain text or numbers as follows: Cell A 2, Salesperson 1. Cell B 2, 2,300 dollars. Cell C 2, 115 dollars. Cell E 2, 5.00 percent. Cell A 3. Salesperson 2. Cell B 3, 1,800 dollars. Cell A 4, Salesperson 3. Cell B 4, 2,500 dollars. Cell A 5, Salesperson 4. Cell B 5, 1,700 dollars. Figure 2 represents row 1 columns B, C, and E contain headers that say, in order from B, C, E: "Sales Amount," "Commissions Earned," and "Sales Commission." In subsequent rows, some cells contain text or numbers as follows: Cell A 2, Salesperson 1. Cell B 2, 2,300 dollars. Cell C 2, 115 dollars. Cell E 2, 5.00 percent. Cell A 3. Salesperson 2. Cell B 3, 1,800 dollars. Cell C 2, 0.00 dollars. Cell A 4, Salesperson 3. Cell B 4, 2,500 dollars. Cell C 3, 0.00 dollars. Cell A 5, Salesperson 4. Cell B 5, 1,700 dollars. Cell C 4, 0.00 dollars.
5. A retail store owner pays sales staff a flat hourly rate plus a sales commission of 5%. The store owner creates a spreadsheet and enters the formula =B2*E2 in cell C2 to calculate the commission earned by Salesperson 1, as shown in Figure 1. The store owner then copies the formula from cell C2 into cells C3, C4, and C5. The store owner expects to see the commissions earned by the remaining sales staff, but instead sees the values shown in Figure 2. The source of this problem is most likely due to an error related to which of the following concepts?
- Cell formatting.
- Circular references.
- Automatic formatting.
- Relative cell referencing.
- Enter to expand or collapse answer.Answer expanded
- Option D is correct. This question requires the examinee to demonstrate knowledge of spreadsheet and database software. Spreadsheet cell references can be either relative or absolute. However, by default, most cell references are relative. For example, when the store owner copies the formula =B2*E2 from cell C2 to C3, the copied formula will appear as =B3*E3 — which maintains the relative relationship between the cells. Note that this equals zero since cell E3 is empty and the spreadsheet interprets an empty cell as zero. A special command must be used to make the cell reference absolute. In some spreadsheets this command would be =B2*$E$2. If this expression were copied to cell C5, for example, it would appear as =B5*$E$2, which would give the desired commission.
6. A graphic designer is creating digital images for a Web site and wants to save the files in a format that supports transparency and lossless compression. Which of the following file formats meets these criteria?
- PNG.
- TIFF.
- GIF.
- JPEG.
- Enter to expand or collapse answer.Answer expanded
- Option A is correct. This question requires the examinee to demonstrate knowledge of the manipulation of audio, video, text, and graphics. Portable Network Graphics (PNG) image format is generally used for Web sites. PNG uses a lossless compression algorithm and offers a variety of transparency options. PNG also supports interlacing, but does not support animation.
Competency 004—Demonstrate a broad and comprehensive understanding of the design, development, and uses of computer-based learning resources, tools, and environments.
7. Electronic information is transferred through the Internet using packet switching technology. Which of the following statements best describes a characteristic of this type of technology?
- The packets are scanned for viruses at each node along the route.
- Each packet can take a different route depending on network load.
- The receiving server passes each packet to the end user as soon as it is received.
- The sending server bundles multiple electronic messages together into a single packet.
- Enter to expand or collapse answer.Answer expanded
- Option B is correct. This question requires the examinee to demonstrate knowledge of Internet concepts and terminology. The Internet protocol TCP/IP uses packet switching technology. When a message is to be sent over the Internet, it is broken up into many packets, each containing the address of the source and the destination. The packets are then routed over the Internet, from node to node, to their recipient. During transport over the Internet, packets may be sent out of order and may take different network paths. The packets are assembled back together at the final destination.
8. A Web designer would typically use client-side scripting to accomplish which of the following tasks?
- Linking to a video clip on another Web site.
- Displaying an animated GIF graphic.
- Detecting the type of browser a visitor is using.
- Responding to user-entered data from an HTML form.
- Enter to expand or collapse answer.Answer expanded
- Option C is correct. This question requires the examinee to demonstrate knowledge of principles of Web page design. A client-side scripting language is a programming language that is used to write computer programs that are executed on the client's (i.e., the user’s) Web browser. Client side scripts are used to provide some level of interactivity. One common use of a client-side scripting language is to detect the type of browser a Web site is using so that browser-specific features can be addressed.
Competency 005—Demonstrate a broad and comprehensive understanding of concepts and skills related to computer programming.
Use the code segment below to answer the question that follows. 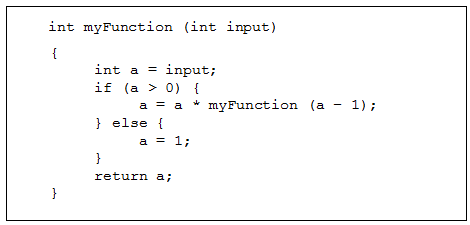
int my Function left parenthesis int input right parenthesis
open left curly bracket
int a equals inputs;
if left parenthesis a greater than 0 right parenthesis open left curly bracket
a equals a times my Function left parenthesis a minus 1 right parenthesis semicolon
close right curly bracket else open left curly bracket
a equals 1 semicolon close right curly bracket
return a semicolon close right curly bracket
9. When the integer 5 is passed to the function myFunction, which of the following expressions represents the returned value?
- 5 times 4
- 5 squared
- left parenthesis 5 minus 1 right parenthesis squared
- 5 factorial
- Enter to expand or collapse answer.Answer expanded
- Option D is correct. This question requires the examinee to demonstrate knowledge of computational thinking. The function shown is a recursive function since it calls itself. If the number 5 is input, the following will occur. Since 5 is greater than zero, a = 5*myFunction(4). But myFunction(4) = 4*myFunction(3), and myFunction(3) = 3*myFunction(2), and myFunction(2) = 2*myFunction(1), and myFunction(1) = 1*myFunction(0) = 1, since myFunction returns 1 if it is passed the value of 0. Hence the function will return a = 5*4*3*2*1 = 5 factorial
10. A computer program is being designed to manage employee information. The program uses the superclass Employee and the subclass SalesAgent. Which of the following statements best illustrates the concept of inheritance in these classes?
- An object of type SalesAgent can be made by converting an object of type Employee.
- The subclass SalesAgent contains the characteristics of Employee as well as characteristics unique to SalesAgent.
- All functions within the subclass SalesAgent must also exist in Employee.
- The fields within an object of type SalesAgent can only be accessed through functions in the Employee superclass.
- Enter to expand or collapse answer.Answer expanded
- Option B is correct. This question requires the examinee to demonstrate knowledge of the software development process, including object-oriented design. Inheritance is a major characteristic of object-oriented design. The superclass Employee will have fields and methods, and these characteristics will be inherited by the subclass SalesAgent. However, a subclass can also have its own methods and fields, so it will be possible for SalesAgent to have its own unique characteristics to address any special job responsibilities of an employee who is a sales agent.
Use the table below to answer the question that follows.
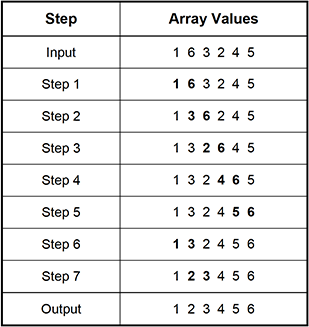
The first row contains the following headings: column 1, Step. Column 2, Array Values. Row 2 represents Input, with array values of 1, 6, 3, 2, 4, 5. Row 3 represents Step 1, with array values of 1, 6, 3, 2, 4, 5. Row 4 represents Step 2, with array values of 1, 3, 6, 2, 4, 5. Row 5 represents Step 3, with array values of 1, 3, 2, 6, 4, 5. Row 6 represents Step 4, with array values of 1, 3, 2, 4, 6, 5. Row 7 represents Step 5, with array values of 1, 3, 2, 4, 5, 6. Row 8 represents Step 6, with array values of 1, 3, 2, 4, 5, 6. Row 9 represents Step 7, with array values of 1, 2, 3, 4, 5, 6. Row 10 represents Output, with array values of 1, 2, 3, 4, 5, 6.
11. The steps used by a sorting function to arrange an array of integers into ascending order are shown in the table. The sorted values at each step in the function are indicated in bold. Which of the following types of algorithms is being used in this function?
- bubble sort
- insertion sort
- merge sort
- selection sort
- Enter to expand or collapse answer.Answer expanded
- Option A is correct. This question requires the examinee to demonstrate knowledge of fundamental algorithms, such as sorts. Close analysis of the algorithm indicates that it examines each pair of adjacent integers and checks to see if they are in the correct order. If they are it goes to the next pair, and if they are not, it puts them in order and then goes to the next pair. It continues in this way through the one-dimensional array. After it has gone through the array once, it goes through the array again until no exchanges are needed. This is the characteristic of the bubble sort algorithm.
Domain III—Computer-Based Technology in Society
Competency 006—Demonstrate a broad and comprehensive understanding of the appropriate use of computer technology and the interrelationships between technology and society.
12. The first network of interconnected computers that was the precursor to the modern Internet was developed through funding from:
- the U.S. Department of Defense.
- the telecommunications industry.
- the National Aeronautics and Space Administration (NASA).
- a consortium of technology institutes.
- Enter to expand or collapse answer.Answer expanded
- Option A is correct. This question requires the examinee to demonstrate knowledge of the historical development and important trends affecting the evolution of technology. The design and building of the Internet was funded by ARPA (now called DARPA), the Advanced Research Projects Agency which was part of the U.S. Department of Defense. The goal was to create a robust communications network that could send data across a variety of routes in case of failure. The progenitor of the Internet was ARPANET, which used packet switching technology and had many of the features of today's Internet.
13. A student is creating and publishing a Web site for a class project. The student would like to include in the project a photograph found on a commercial Web site. The student cannot find a copyright statement on the commercial Web site. Which of the following statements best describes the student's responsibility in this situation?
- If the image appears on the site's home page, the student is free to download and use the photograph if he credits the source.
- Since there is no copyright information on the site, the student is free to download and use any images appearing there as if they were his own.
- The student is free to download and use the photograph as long as he makes at least one minor revision to the photograph.
- The student must receive permission from the site's owner before downloading and using the photograph.
- Enter to expand or collapse answer.Answer expanded
- Option D is correct. This question requires the examinee to demonstrate knowledge of the ethical and appropriate use of digital information, including issues related to copyright. Copyright laws govern the use of material on the Internet. While some aspects of copyright law are subtle and complex, current law states that neither publication nor a notice of any kind is needed to protect original work. This means that any material posted to the Internet has automatic copyright protection and cannot be used without permission from the site's owner, unless the site provides permission.
